Docker File Best Practices For DevOps Engineer
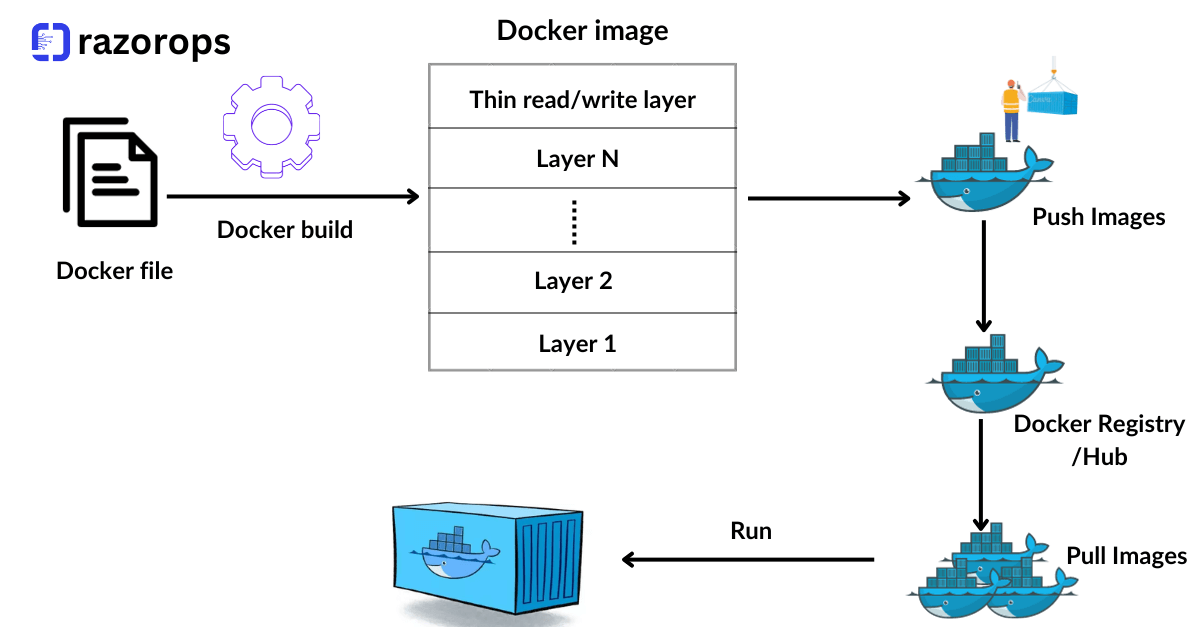
Containerization has become a cornerstone of modern software development and deployment. Docker, a leading containerization platform, has revolutionized the way applications are built, shipped, and deployed. As a DevOps engineer, mastering Docker and understanding best practices for Dockerfile creation is essential for efficient and scalable containerized workflows. Let’s delve into some crucial best practices to optimize your Dockerfiles.
i. Start with a Clear Base Image:
Choose a base image that aligns with your application’s requirements. Utilize official images whenever possible as they are regularly updated and maintained, ensuring better security and reliability.
ii. Use Specific Tags for Base Images:
Be specific with the tags used for base images (e.g., ‘alpine:3.14’ instead of ‘alpine:latest’). This ensures consistency across builds and avoids unexpected changes due to updates.
iii. Optimize Image Layers:
Leverage the Docker layer caching mechanism by ordering commands efficiently in your Dockerfile. Put frequently changing steps towards the end to maximize caching benefits.
iv. Reduce Image Size:
Minimize the image size by removing unnecessary dependencies, unused packages, and temporary files in the final image layers. Utilize multi-stage builds to keep the final image lean.
v. Security is Paramount:
Regularly scan images for vulnerabilities using tools like Clair, Trivy, or Docker Security Scanning. Ensure that only necessary ports are exposed, and sensitive information isn’t hardcoded within the image.
vi. Use .dockerignore:
Similar to .gitignore, create a .dockerignore file to exclude unnecessary files and directories from being copied into the Docker image. This reduces build time and prevents unnecessary bloat.
vii. Avoid Running Containers as Root:
Whenever possible, create a non-root user within the container and run the application as that user. This mitigates security risks associated with running processes as the root user.
viii. Keep Dockerfile Readable and Documented:
Maintain clarity and readability in your Dockerfile. Use comments to explain complex or critical steps. This aids collaboration and troubleshooting for you and your team.
ix. Version Control Dockerfiles:
Store Dockerfiles in version control systems like Git to track changes, facilitate collaboration, and ensure reproducibility of builds across different environments.
x. Automate Image Builds:
Implement Continuous Integration (CI) pipelines to automate the build, test, and deployment of Docker images. Tools like Jenkins, GitHub Actions or Razorops CICD https://razorops.com/ can help streamline this process.
xi. Regularly Update Images:
Stay updated with security patches and new releases of base images. Set up a process to periodically rebuild and redeploy containers to incorporate these updates.
xii. Test Docker Images Thoroughly:
Before deployment, conduct rigorous testing of Docker images in various environments to ensure compatibility and reliability.
1. Use Official Base Images
When crafting a Dockerfile, start with official base images provided by Docker or trusted repositories like Alpine, Ubuntu, or Debian. These images are well-maintained, regularly updated, and thoroughly tested for security vulnerabilities. They serve as a solid foundation for your containers, reducing security risks and ensuring stability.
FROM debian:bullseye
2. Leverage Layer Caching
Utilize Docker’s layer caching mechanism to expedite the build process. Place frequently changing instructions towards the end of your Dockerfile to leverage caching. This approach allows Docker to reuse intermediate layers from previous builds, saving time during subsequent builds.
COPY . /app
RUN npm install # Frequent changes should come after this line
3. Minimal and Specific Dependencies
Keep Docker images lightweight by including only necessary dependencies. Use specific package versions to prevent unexpected changes and ensure reproducibility across environments. Remove unnecessary files and dependencies after installation to reduce image size.
<code>
RUN apt-get update
&& apt-get install -y –no-install-recommends
package1=version
package2=version
&& apt-get clean
&& rm -rf /var/lib/apt/lists/*
</code>
4. Single Responsibility Principle
Adhere to the Single Responsibility Principle by creating specialized images for different services or components. Each container should focus on one task or service, enabling scalability and ease of management.
# Web server container
FROM nginx:latest
# Configuration and setup
…
5. Optimize Layer Ordering
Order your Dockerfile commands logically to enhance readability and maintainability. Group related commands together and use multi-stage builds to separate build-time dependencies from the final production image.
# Build stage
FROM node:latest AS build
WORKDIR /app
COPY package.json.
RUN npm install
COPY..
RUN npm run build
# Production stage
FROM nginx:latest
COPY –from=build /app/build /usr/share/nginx/html
6. Security Best Practices
Prioritize container security by regularly updating base images and dependencies. Implement security scanning tools to identify vulnerabilities within your Docker images. Avoid running containers with root privileges and utilize user namespaces when possible.
7. Test and Validate
Thoroughly test Dockerfiles to ensure they function as expected. Automate image building and testing processes within Continuous Integration/Continuous Deployment (CI/CD) pipelines to catch issues early in the development cycle.
In conclusion, Dockerfile best practices involve optimizing images for efficiency, security, and maintainability. By following these guidelines, DevOps engineers can create robust, lightweight, and secure Docker images, facilitating seamless application deployment and management.
Start implementing these best practices today and unlock the full potential of Docker for your DevOps workflows! Follow RazorOps Linkedin Page Razorops, Inc.